Schedule¶
Warning
ARCHIVED PAST COMPETITION, FOR REFERENCE ONLY
Phases¶
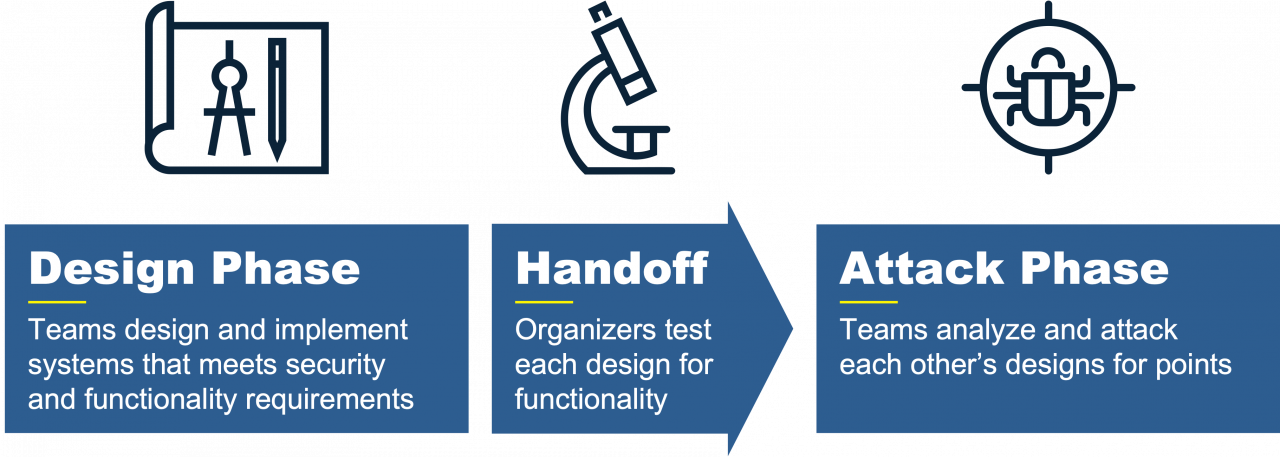
Design Phase Teams design and build their own design
Handoff: Teams turn in their design to the eCTF organizers for testing
Attack Phase: Teams that have passed Handoff can earn points by attacking the designs of other teams in the Attack Phase
Important Dates¶
January 15: Competition Kickoff, Design Phase begins
February 26: Handoff begins
April 16: Scoreboard closes, flags no longer accepted
April 25: Award Ceremony
Design Phase Flags Due Dates¶
See Design Phase Flags for details.
January 22: Read the Rules
January 24: Boot Reference
January 31: Initial Design Document
February 7: Use Debugger
February 14: Testing Service
February 26: Attack the Reference Design
Workshop Schedule¶
The eCTF organizers will hold routine workshops to provide competitors with information about different parts of the competition. Monitor the announcements channel on Slack for details.
January 16: Rules & Reference Design Overview
January 21: Boot Reference Design
January 23: Design Document
January 30: Docker Introduction
February 4: Debugger Walkthrough
February 6: Attack the Reference Design
February 11: Testing Service
February 14-16: BCI Training: Embedded Reversing and Exploitation
February 20: Handoff Preparation
BCI Training: Embedded Reversing and Exploitation¶
eCTF Supporter Boston Cybernetics Institute returns this year to offer a free, 3-day course for all competitors. The course runs from 9am - 5pm on February 14th, 15th, and 16th.
This is a 3-day, hands-on course on reverse engineering and exploiting embedded binaries. Exercises will be across multiple architectures (PowerPC, MIPS, ARM, x86, and x64), and balances fundamentals with modern applications. Exercises will focus on Linux programs and will include various firmware. After completing this course, students will have the practical skills to begin identifying vulnerabilities in embedded systems software and write exploits for those vulnerabilities.
A VM and Zoom information will be posted at the following link at 9am on February 10th: Link
Instructor bio: Jeremy Blackthorne (@0xJeremy) is an instructor and security researcher at BCI, focused on vulnerability assessment and offensive cyber operations. Before that, he was researcher in the Cyber System Assessments group at MIT Lincoln Laboratory. Jeremy has published research at various academic and industry conferences. He served as a rifleman and scout sniper in the U.S. Marine Corps with three tours in Iraq. He has a BS in Computer Science from University of Michigan-Dearborn and a MS in computer science from Rensselaer Polytechnic Institute.
Schedule and Events