Attack Phase Flags and Scenarios¶
Warning
ARCHIVED PAST COMPETITION, FOR REFERENCE ONLY
Tip
Understanding the contents of this page is critical to properly securing your design. If something is unclear, please reach out to the organizers on Slack to clarify.
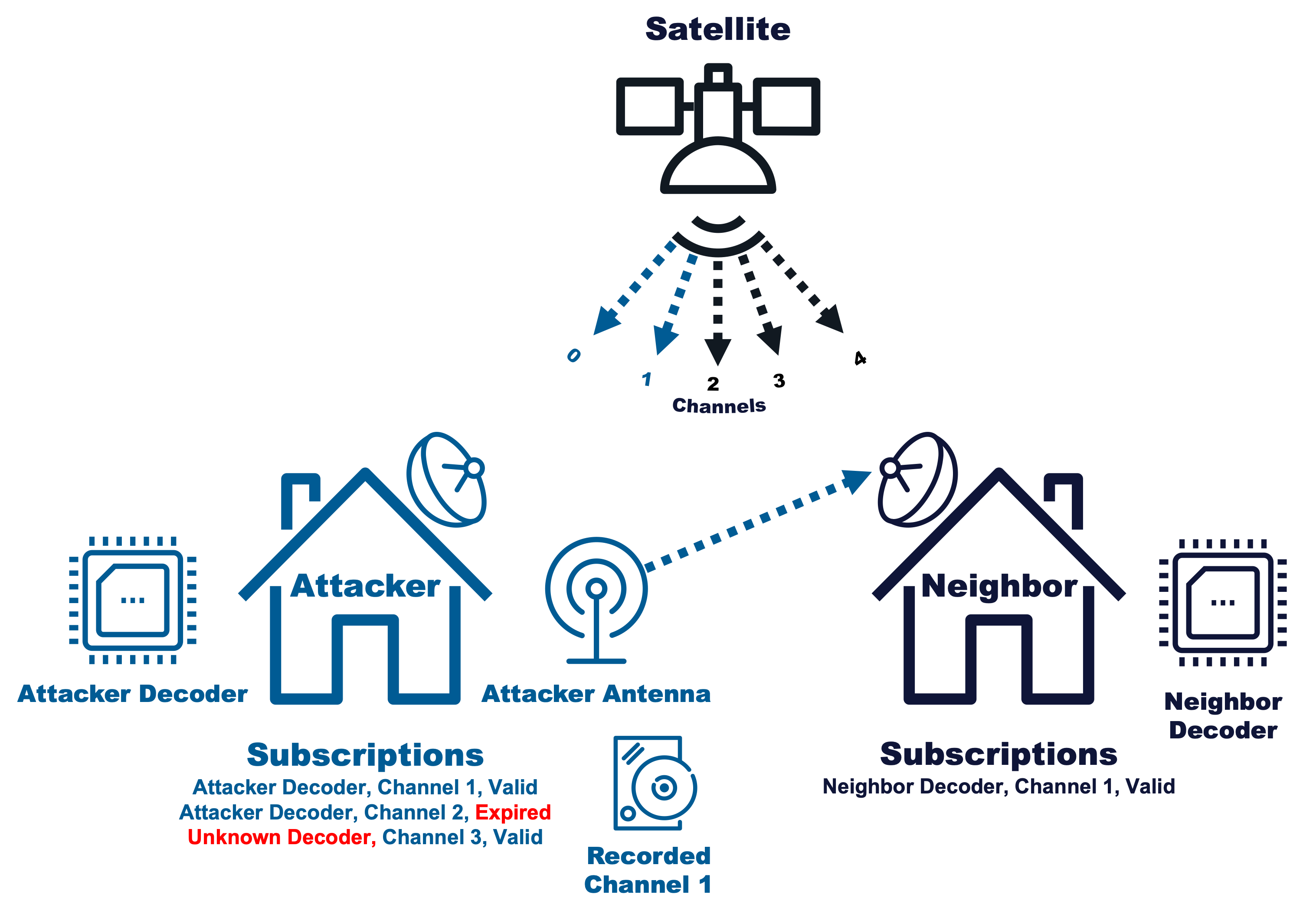
Attack Phase Scenarios¶
Attackers will have access to a number of different subscription updates for a Decoder. Each setup represents a realistic scenario that will test a design’s success at meeting one or more Security Requirements by embedding Attack Phase Flags into different parts of the setup.
This year, the Attack Phase scenarios use a single deployment, with a single satellite transmitting across five channels. The images below summarize the flags, scenarios, relevant security requirements, and deployments.
Attack Phase Flags¶
During the Attack Phase, teams will test the security of other teams’ designs by attempting to capture Attack Phase Flags. Each flag represents proof on an attacker’s ability to compromise one or more security requirements of a design.
Flag |
Format |
Description |
|---|---|---|
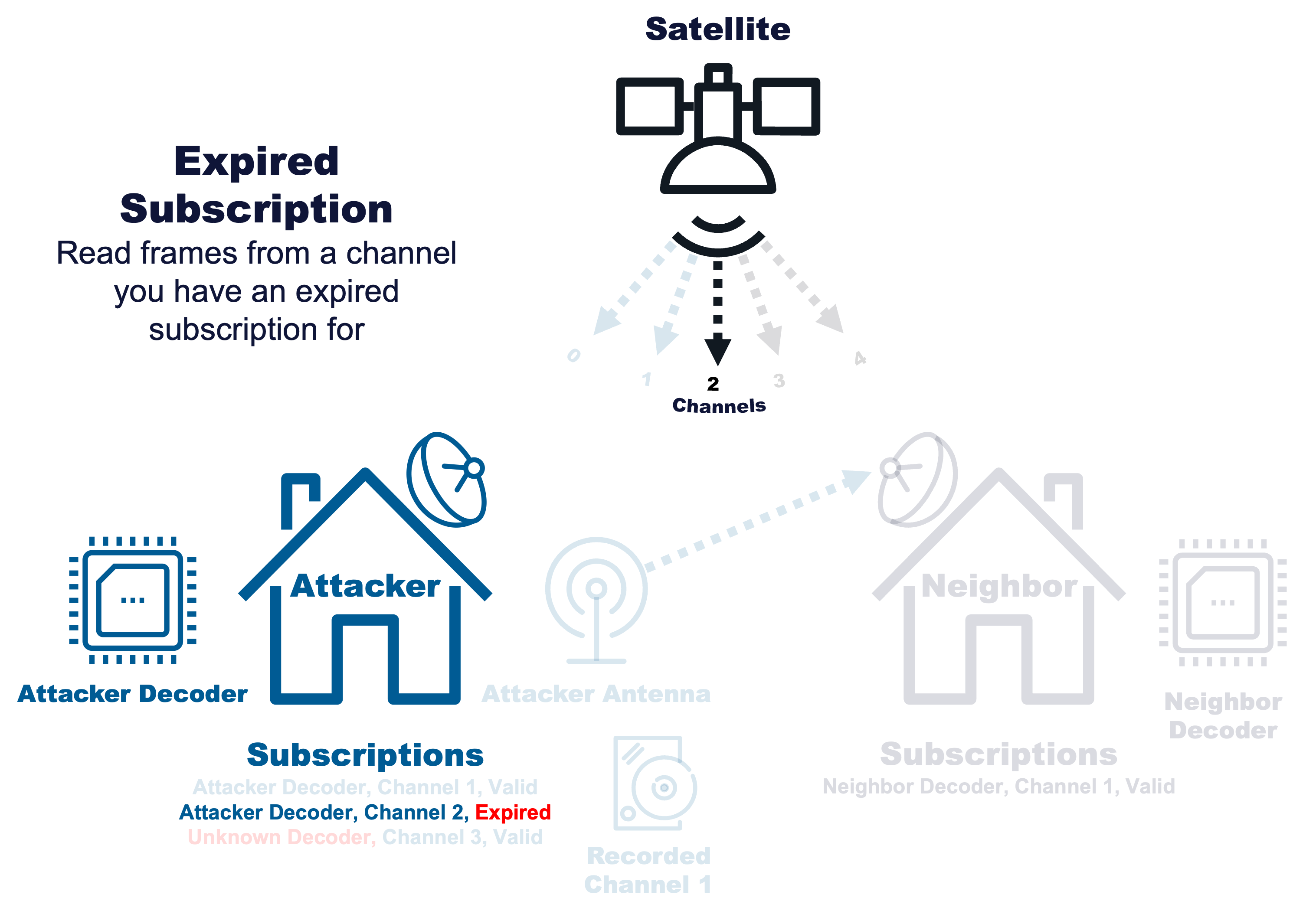
Expired Subscription |
|
Read frames from a channel you have an expired subscription for |
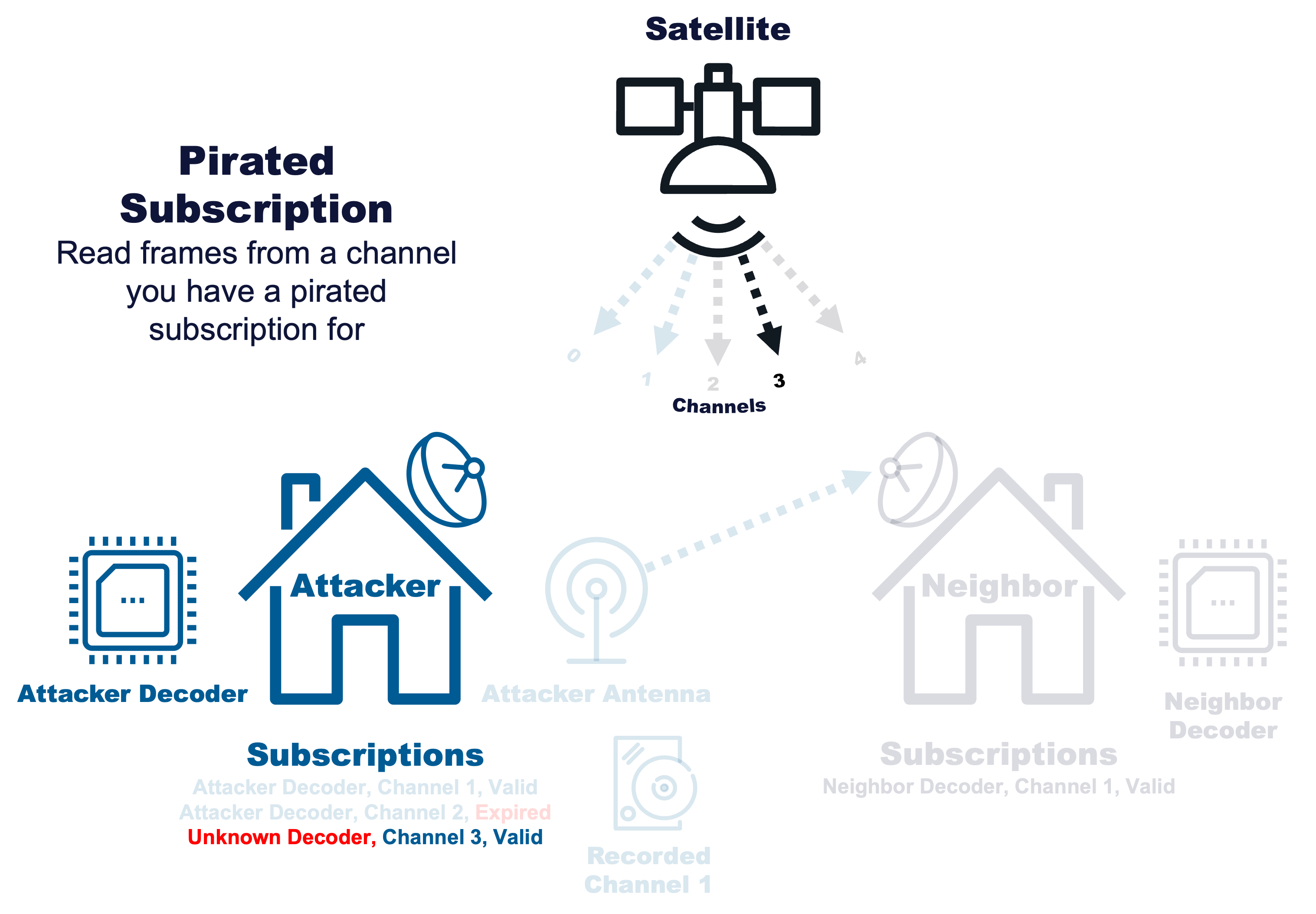
Pirated Subscription |
|
Read frames from a channel you have a pirated subscription for |
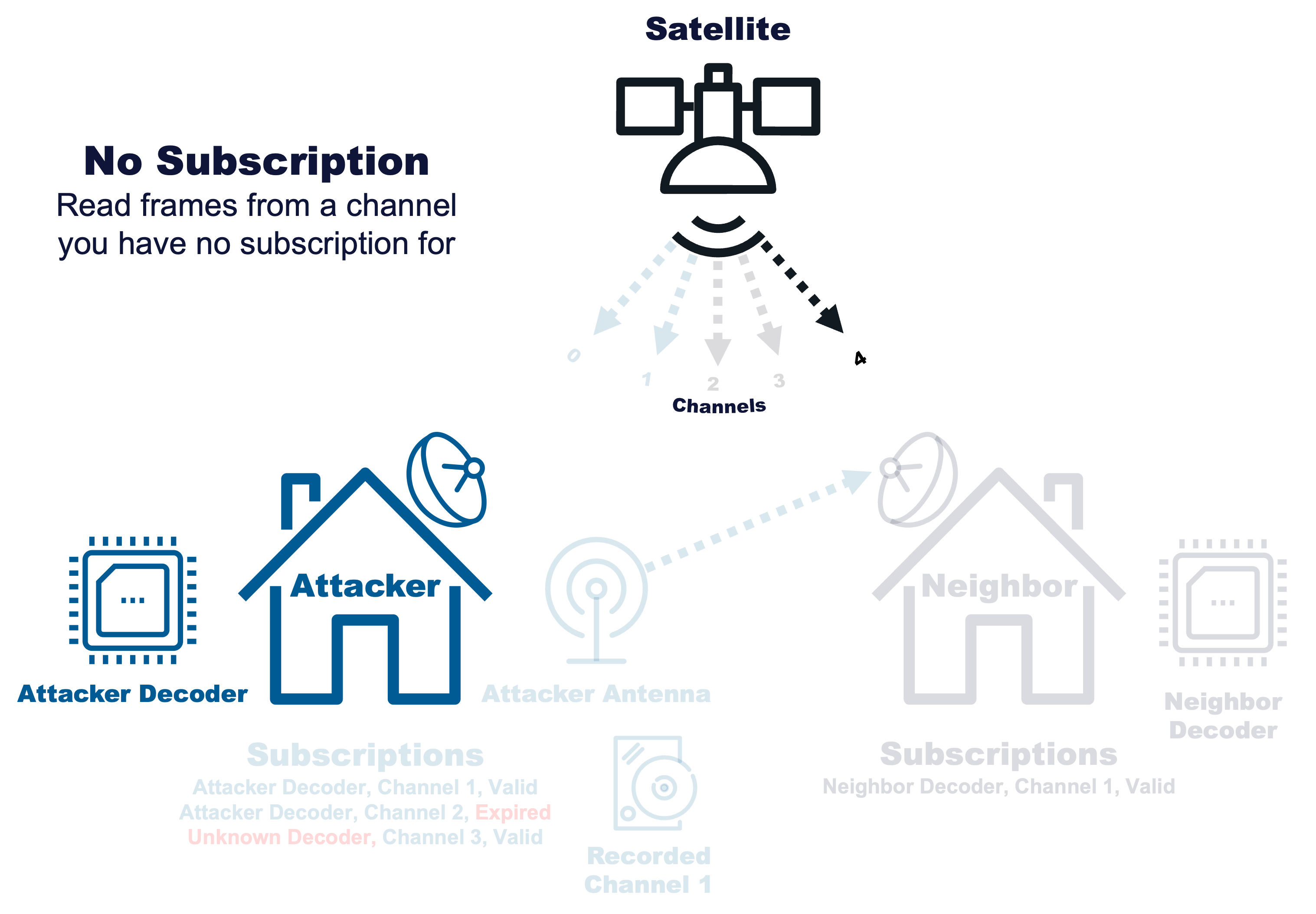
No Subscription |
|
Read frames from a channel you have no subscription for |
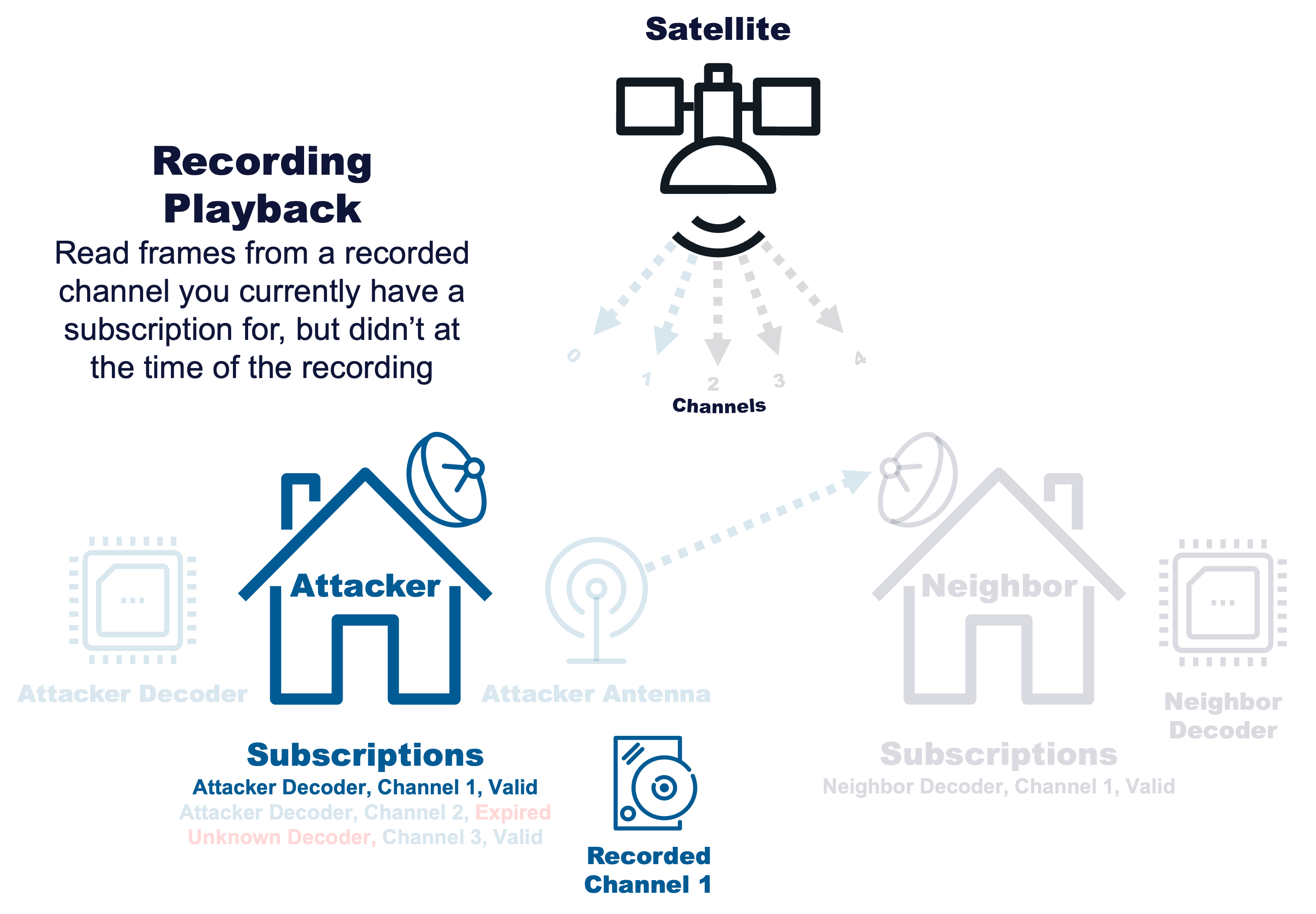
Recording Playback |
|
Read frames from a recorded channel you currently have a subscription for, but didn’t at the time of the recording |
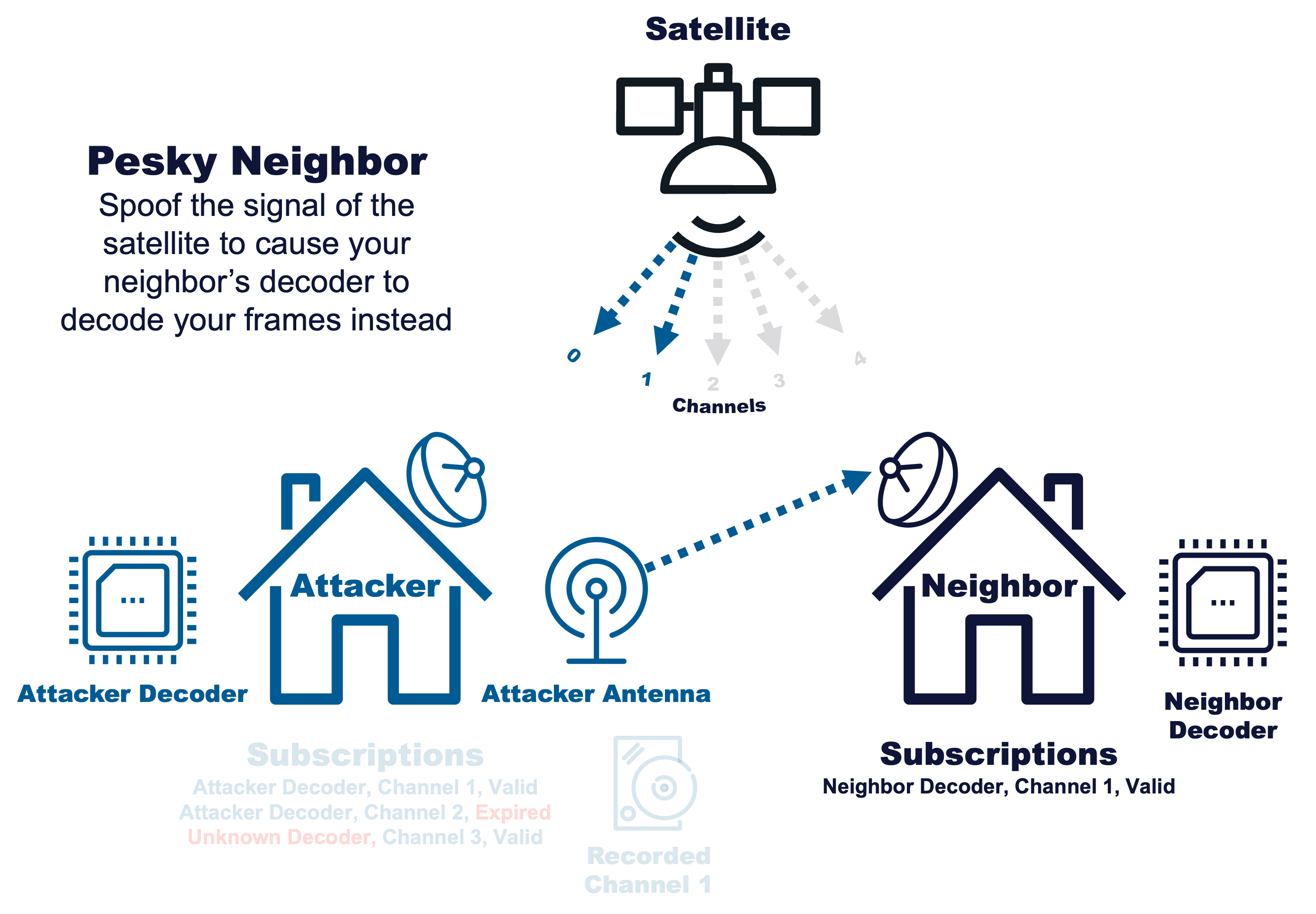
|
Spoof the signal of the satellite to cause your neighbor’s Decoder to decode your frames instead |